A Simple Guide to Multi-Factor Authentication for the Enterprise by Davey Winder
According to the latest Verizon Data Breach Investigations Report 21% of incidents involved the use of stolen login credentials. Analysis from multiple threat intelligence sources has confirmed what we’ve all been thinking: the ransomware threat is on an upward curve. Attacks in the UK have doubled in the first six months of 2021 alone, while globally, there has been a 900% increase.
Ransomware threat actors favour the path of least resistance
The attack that propelled the ransomware threat onto a global stage, that on Colonial Pipeline that badly disrupted fuel supplies across the East Coast, reportedly started with a single compromised password. The growth of the ransomware threat to the enterprise is reflected in the development of the Initial Access Broker (IAB) marketplace. This is where compromised network access details are sold to the highest criminal bidder, most often ransomware gang affiliates who are responsible for getting that initial access to your enterprise that empowers the attackers.
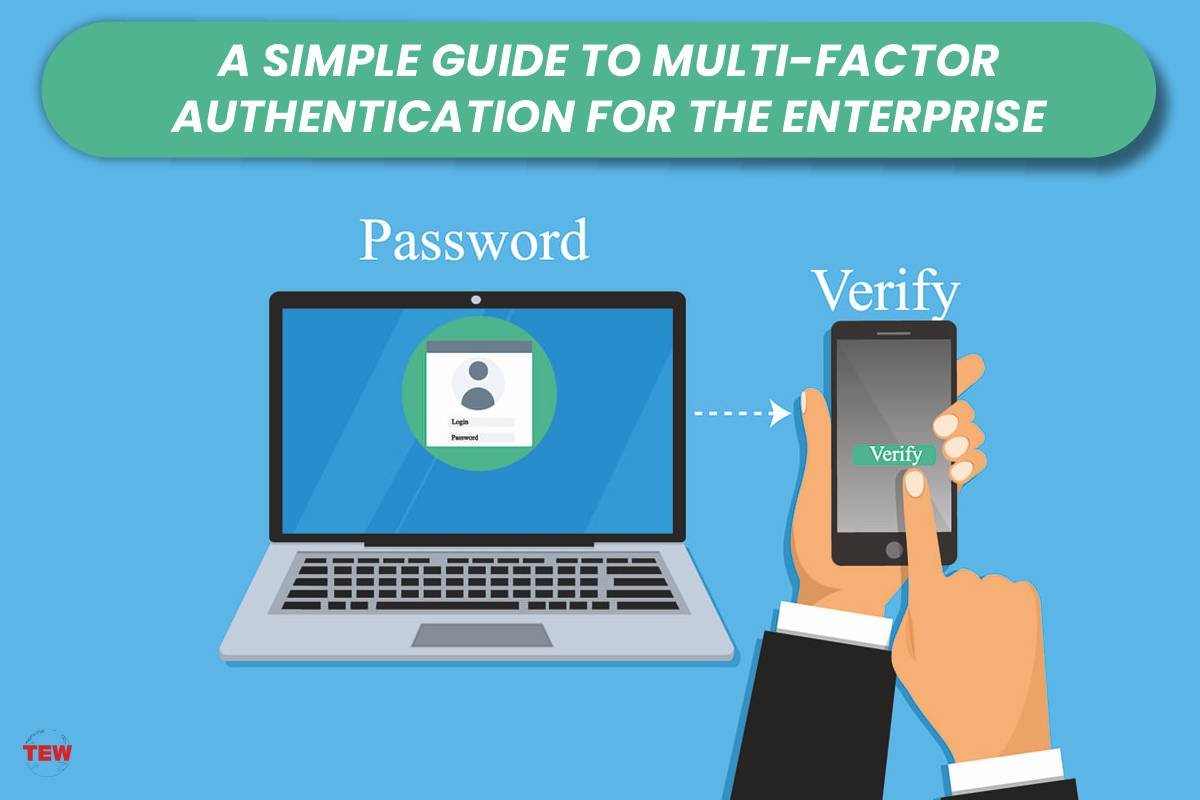
By now, alarm bells should be ringing for all enterprise security teams, not least as there’s a relatively simple stumbling block, or blocks to be more precise, that can be erected in the path of such cyber criminals: multi-factor authentication (MFA).
Three Multi-Factor Authentication essentials:
1. Do the Risk Math
Recent research has confirmed the reality of poor password hygiene in the workplace. Some 41% of employees admitted to sharing workplace passwords, and 20% used work passwords for personal accounts, further expanding the threat. Adding more authentication factors than simply a username and password combination should, therefore, be a no-brainer. The risk math is straightforward enough: each additional factor reduces the chances of attack success. MFA mitigates the credential compromise domino effect by placing hurdles that most threat actors will be unable to jump.
2. Combine Factors from Different Core Categories
The key is ensuring that each factor comes from a different category: knowledge (what you know), possession (what you have), inherence (what you are), location (where you are) and behaviour (what you do). Take two-factor authentication as an example, usually applied using knowledge (username and password) plus possession (hardware key, one-time code, smartcard). However, using smartphones as a vehicle for accessing that secondary factor can also bring inherence to the party by way of facial or fingerprint recognition in a two-for-one scenario.
3. Multi-Factor Authentication All The Things
Don’t confuse authentication with authorisation as the latter permits users to access a device or service, whereas what we’re talking about, authentication, serves to confirm a user is who they claim. Although it’s tempting to think that only ‘privileged users’ need to be protected by multiple authentication factors, this would be poor risk management when the low hanging fruit of ordinary employees is often picked by threat actors looking for an easy way to get on the threat escalation ladder. Any enterprise aspiring to a strong security posture should be looking at multi-factor authentication solutions, be that two-factor authentication (2FA) or beyond.
Evolution, Not Revolution, Makes MFA a Reality for Every Enterprise
Writing at Forbes, security researcher David Balaban rightly points out that authentication technology itself is evolving at a rapid pace. “Modern authentication,” he writes, “goes beyond the traditional concepts of knowledge, possession, and inherence and involves capabilities such as adaptive and contextual attributes, UEBA (User and Entity Behaviour Analytics), trust assessment and passwordless authentication.”
More often than not, introducing multiplicity into a technical issue is a bad thing, but that’s not the case here. Not least as what we are talking about is providing not only more but better options when it comes to securing the authentication process. So, while the technology evolution continues, it’s not so revolutionary as to create confusion. Combining risk scoring with policy-based access and ‘traditional’ two-factor authentication methods with the developments above combine to create what you might call a multi-factor universe of options. The more options, the more likely a combination will work for your enterprise, within your budget and without creating user roadblocks.
The National Cyber Security Centre (NCSC) recommends https://www.ncsc.gov.uk/collection/device-security-guidance/infrastructure/enterprise-authentication-policy that enterprise authentication models should choose those factors which maximise usability whilst providing the appropriate levels of security. However, the NCSC advises clear and pragmatic policies and guidance to back them up whatever you choose. This is excellent advice as usability issues and cost, the latter triggered by overly complex solutions, are the enemies of successful multi-factor authentication adoption.
Grasping the Identity and Access Management Nettle
What multi-factor authentication isn’t is a security panacea; it should not and cannot be seen, somewhat ironically, as a singular solution to the secure access problem. Instead, it should be considered part of a bigger identity and access management (IAM) picture that may include single sign-on (SSO) and passwordless technologies. FIDO2 is an excellent example of where passwordless authentication fits into all of this, for example. A collaboration between the FIDO Alliance and the World Wide Web Consortium, it’s the latest set of specifications for the Fast ID Online (FIDO) authentication protocol.
As Danna Bethlehem Coronel, identity and access management specialist with Thales, explains, “Based on public-key cryptography,” it provides “a high level of security while easing the login experience for users.” Let’s all agree that has to be a good and secure thing. The unprecedented shift to work-from-home requirements that the pandemic brought with it has had the effect of bringing the benefits of MFA into sharp focus for more enterprises than ever; now, we must ensure this risk-based access nettle is firmly grasped moving on.
About The Author- Davey Winder
Davey is a freelance technology journalist and a senior contributor to Forbes, as well as being contributing editor at PC Pro magazine. He was named ‘Cyber Writer’ of the year in the 2020 Security Serious Unsung Heroes awards. He also contributes to InfoSecurity Magazine, SC Magazine UK, The Observer/Guardian, and Digital Health Intelligence.