According to Gartner, AWS dominates the global IaaS market, with over 38% percent market share. One of the reasons is that AWS helps companies deploy software more quickly and efficiently and smoothly scale workloads on demand.
For instance, AWS DevOps services adoption enables companies to build CI/CD pipelines and automate code delivery and deployment, helping mitigate software downtime during updates. Some can go even further by implementing DevSecOps practices and thus significantly improve software security.
This article covers the concept of DevSecOps and highlights how companies can set it up in AWS.
Why adopt DevSecOps?
Like traditional DevOps, the DevSecOps culture implies a close collaboration between development and IT operations teams to streamline software deployment. However, DevSecOps suggests implementing security controls early in the development stage and using testing mechanisms at every step of code creation.
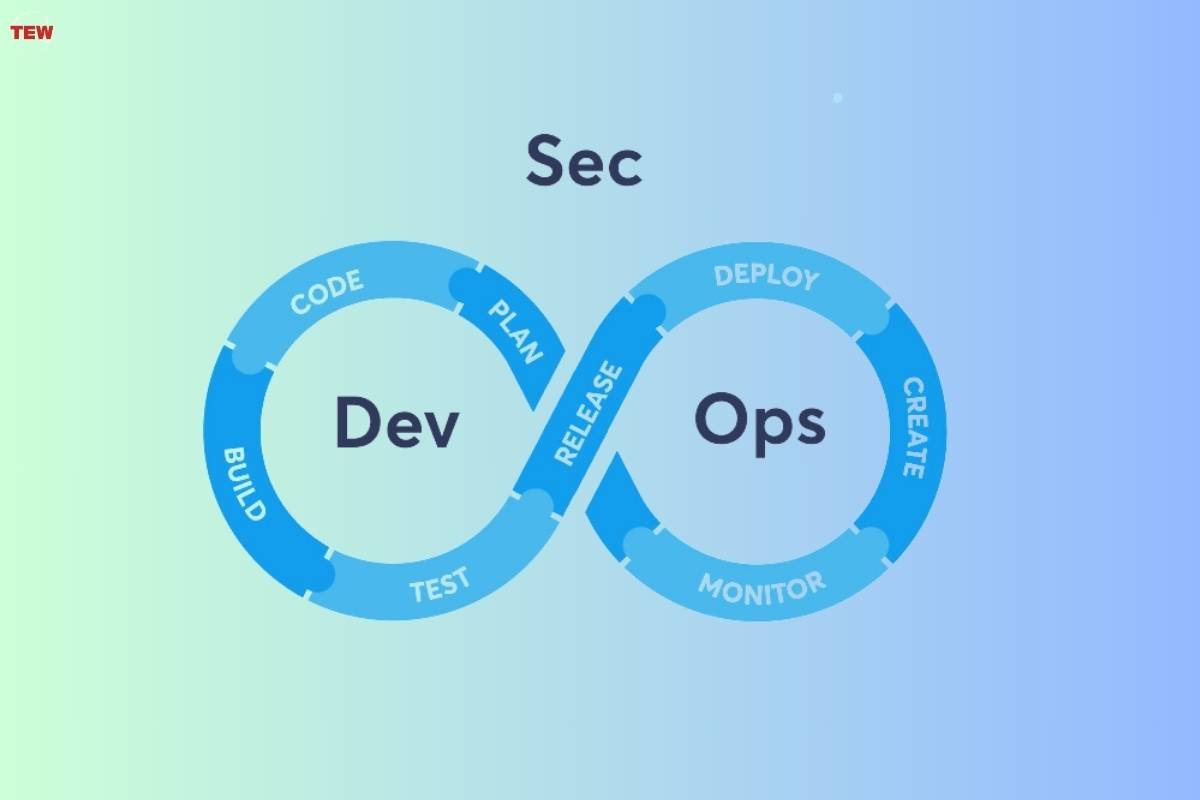
Therefore, the concept can be considered an evolution from traditional DevOps, which primarily focuses on improving release speed and frequency. In practice, implementing DevSecOps can provide companies with the following business benefits:
1. More secure code
With DevSecOps, developers identify errors and vulnerabilities in the code quicker and earlier, eliminating them as soon as they appear. This can significantly improve the security of the final product.
2. Improved cyber security awareness
DevSecOps assumes that each team member (including development, operations, and security specialists) is responsible for the solution’s security. This makes team members more familiar with the best security practices and helps identify potential threats in the code faster.
3. Advanced automation and standardization
At the heart of DevSecOps are repeatable and automated processes (such as tests and monitoring) that help ensure the security of the developed solution. Also, the standardization makes it easier to continuously scale the use of DevSecOps practices.
How to enable DevSecOps with AWS?
Establish a DevSecOps pipeline
The principles of continuous integration and deployment (CI/CD) are fundamental to DevOps, and DevSecOps is no different here. To ensure the effective use of DevSecOps practices, companies must integrate the ones for each stage of their AWS CI/CD pipelines, and here is how it can look in practice.
1. Plan
The official OWASP guidelines suggest implementing such techniques as threat modelling, or identifying all potential security risks to a product, early on. As a result, teams can compile a complete list of threats and address them in advance with proper security measures.
In addition, this information allows teams to create comprehensive plans defining when and how security testing should be performed throughout the project. Teams can use relevant solutions from the AWS Marketplace, such as IriusRisk, to integrate threat modeling into their SDLC. IriusRisk automates the building of threat models and helps address vulnerabilities throughout development.
2. Code

To ensure security during the coding phase, teams can adhere to defensive programming principles within the DevSecOps pipeline. In a nutshell, this concept involves the early detection and isolation of errors in the code, thereby ensuring predictable and stable software operation in the future.
To realize this concept, developers can implement tools such as formatters and linters, like AWS CloudFormation Linter to check AWS CloudFormation templates, highlight suspicious bugs or errors, and eliminate them timely.
3. Build
The build phase begins after developers create the code and submit it for version control. In this step, DevSecOps focuses on analyzing the source code and its dependencies against the most common vulnerabilities, which helps detect and prevent them.
At this stage, one of the most essential DevSecOps practices is SAST (static software application testing). Applicable to all programming languages, this technique allows testing specialists to identify mathematical and syntax errors in the code without executing it.
One of the advantages of SAST is the ability to be smoothly integrated into the existing development process. For example, developers can use Amazon CodeGuru’s interface to integrate CodeGuru Reviewer (an automated code analysis service) with a build automation solution, such as Jenkins or TeamCity.
4. Test
The next step is to test the artifact (an object in the application) consisting of the compiled source code deployed to the test environment. Here, such DevSecOps techniques as DAST (dynamic application security testing) can come in handy.
Using DAST, testers simulate malicious attacks and try to find software vulnerabilities. This way, DevSecOps teams can understand how the product will perform in a real-world environment.
Today, the AWS Marketplace offers more than 30 DAST tools. For example, IT teams can use InsightAppSec, StackHawk, or Fortify on Demand, all providing such features as CI/CD automation and integration with the CI/CD build solutions.
5. Deploy
After deploying a build artifact to production, teams must verify and update TLS and DRM certificates while resolving configuration discrepancies between staging and production environments. Here, an IT team can use tools such as AWS Config, as it helps evaluate resource configuration for vulnerabilities and non-compliance. Due to integration across AWS services, teams also can use a unified AWS Security Hub interface to perform this task.
6. Maintain and monitor

After the product has been released and stabilized, teams need to set up automated monitoring to continuously identify threats and data leaks. One of the ways to do this is by implementing RASP (run-time application security protection), a technique that ensures software security during its operation through real-time analysis of code, user behavior, and traffic. Teams can implement RASP using AWS Security Hub and third-party software from the AWS Marketplace, such as Imperva, Falco, or Contrast Security.
Implementing role-based access control (RBAC)
Although DevSecOps implies advanced automation, the role of the human factor remains significant. After all, all development team members are deeply involved in the process of software development and deployment, which creates cyber security risks associated with human error.
Companies can implement models such as RBAC into their DevSecOps infrastructure to address this issue. In short, RBAC allows limiting the access of users (in this case, IT specialists) to data by assigning roles, each related to different network permissions and privileges.
In practice, companies can implement RBAC using the built-in AWS Identity and Access Management. This service manages roles and permissions and determines which team members can access AWS resources and services.
Enhancing data encryption
Finally, we should mention data encryption, one of the critical elements of a DevSecOps strategy. Although AWS automatically encrypts data (objects, buckets) on the server side, companies can additionally implement client-side encryption to ensure advanced security when transferring data from its source to AWS storage.
The easiest way to manage encryption is to use built-in AWS tools such as AWS Key Management Service. This tool allows for managing keys centrally and, being integrated with other AWS services (such as AWS Encryption SDK), can streamline data encryption at all stages of the CI/CD pipeline.
Final thoughts
Despite all the benefits, implementing DevSecOps is challenging and requires advanced technical skills from IT teams. For example, to implement the DAST technique, a company needs specialists with experience in penetration testing.
To overcome this challenge, a company can integrate role-specific training into its SDLC to ensure that developers, testers, and other team members have the necessary skills to perform their duties while ensuring software security. Involving third-party AWS DevSecOps experts and augmenting an in-house IT team with external talent is also a useful option.


















