“How was the network initially compromised?”—This is the question investigators and incident responders hear every time they come to do their job. In fact, these days, most cyberattacks—advanced targeted and otherwise— start from a simple phishing email with a weaponized attachment or web link. In this article, we will examine the most common initial infection vectors and show how Belkasoft helps incident responders and forensic analysts to find the needed evidence.
Note: This paper commenced our Incidence Response series. The Uncovering Cyber Threat Actors’ Persistance Mechanisms with Belkasoft paper came next.
First step: Planning
Before you rush to begin the investigation, it makes sense for you to develop a feasible plan of action.
Where do you start?
Since the typical attack is performed via a phishing email, you can start by checking all the mailboxes on an infected machine (or network) and perusing them for suspicious attachments.
Is that all?
No, malicious code might have been downloaded by a user from a file-sharing service, so you will also do well to search for items with the “sendspace” or “.exe” keyword inside emails. In this regard, a tool capable of creating a full-text index based on millions of emails will be of great help.
Since regular desktop email clients are fast losing their popularity, you must also analyze web-based mail.
If there is nothing in the emails that shows how the endpoint got compromised, you must try to figure out whether an infected USB device was plugged into a computer or if an RDP connection was carelessly exposed to the outer world without proper security measures.
The most common initial infection vectors and show how Belkasoft helps incident responders and forensic analysts find the needed evidence:
- Search for desktop mailboxes
- Search for webmail traces
- Look for attachments in emails
- Look for file-sharing services links distributed via emails •
- Analyze USB device usage history
- Analyze RDP connection
You can refer to other Belkasoft articles to learn how to extend this plan to compensate for more sophisticated attacks and analysis types, but the steps listed here—while being basic—are a must in every incident investigation.
1. Searching for desktop mailboxes
As we earlier stated, delivery via phishing emails is the most common initial infection vector. Therefore, an incident responder must try to identify the source of infection through mailbox parsing. A digital forensic tool that supports computer forensic analysis can help you to achieve this goal.
We will illustrate the search process for emails using Belkasoft Evidence Center X (Belkasoft X). This digital forensics and incident response tool can be used to analyze several email clients.
First, open Belkasoft X and create a new case. You must then add a data source, which can be an image of the compromised computer or laptop. While Belkasoft also allows you to analyze a live computer, this line of action is rarely recommended with an incident investigation case.
After adding the data source, you may opt to analyze it for various artifacts, including email and webmail. This can be done in the following window:
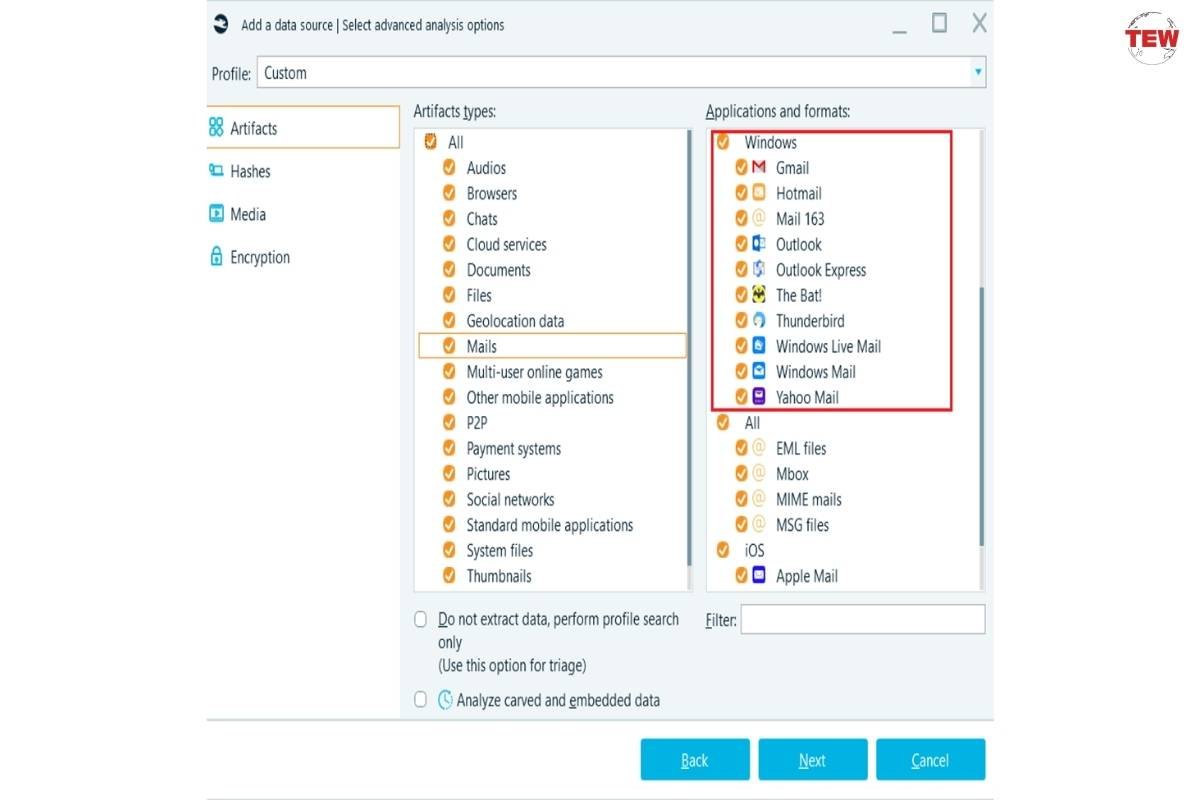
2. Searching for web-based mail traces
Desktop email clients are losing their popularity; a large number of users access their emails on browsers through free services like Gmail. For this reason, your digital forensic software must support webmail artifacts. Belkasoft X can find traces of emails sent on a browser by analyzing memory dumps, disk artifact sources (for example, pagefile.sys), and browsers cache.
To analyze a memory dump or a pagefile, select the corresponding data source type on the Add data source window in Belkasoft X:

3. Looking for attachments in emails
Of course, identification of emails with malicious links is hardly the final step of the investigation. It is imperative that you verify whether the attachment was opened by the user, or if they clicked on a link.
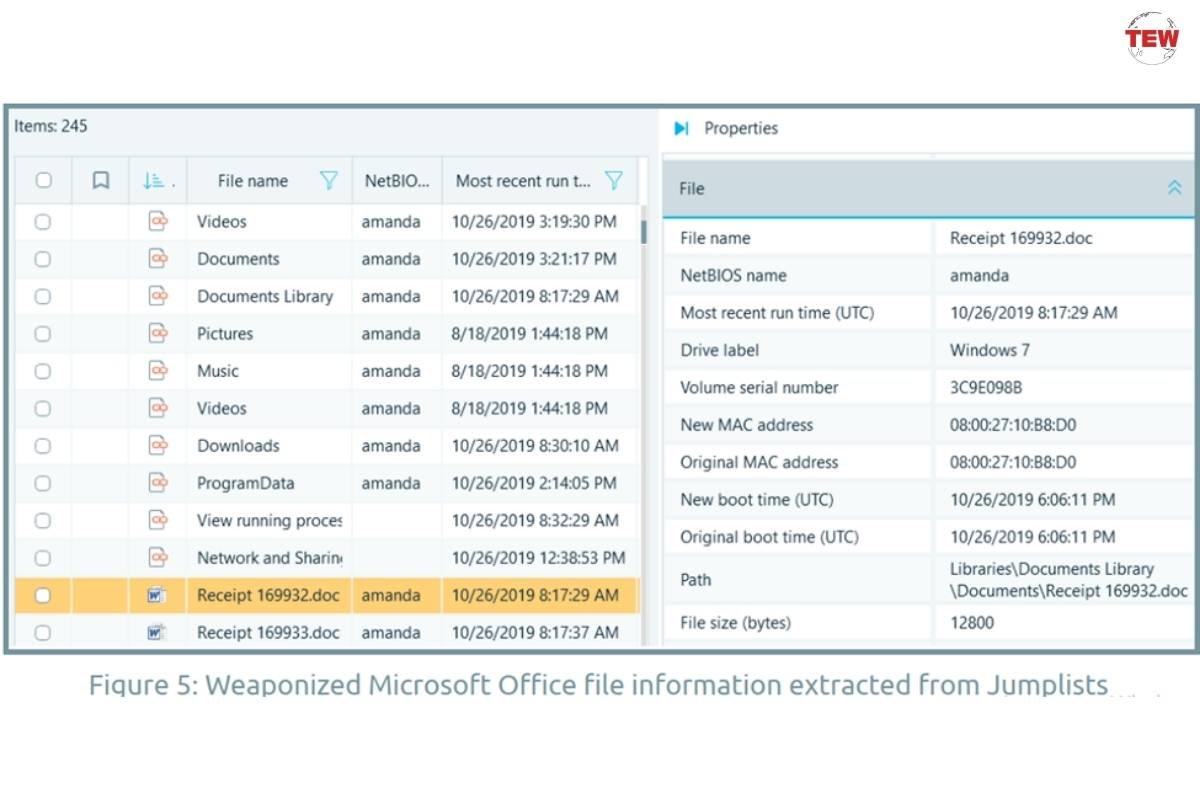
In this case, to retrieve and analyze the needed information, you must check items referred to as “jumplist”. Jumplists are system files that house information about files being opened with a click in Windows Explorer (and other places).
To view jumplist info in Belkasoft X, you must select “Jumplists” under the “System files” node on the artifact selection screen:

In our case, we have found some interesting Microsoft Word files:
4. Looking for file-sharing services links distributed via email
Weaponized attachments are hardly the only source of trouble. Even an email without an attachment could serve as the entry point for an attack. For an incident responder, links to files hosted on file-sharing services—such as Dropbox or SendSpace—constitute interests that must also be investigated.
You will do well to check your image for such links.
Belkasoft X creates a full-text index of data sources added to a case. Once indexing is done, you can perform search tasks.
For the purposes ahead, it is beneficial to create a file with various file-sharing services popular among hackers. You must then instruct Belkasoft X to run searches for all terms from the file:
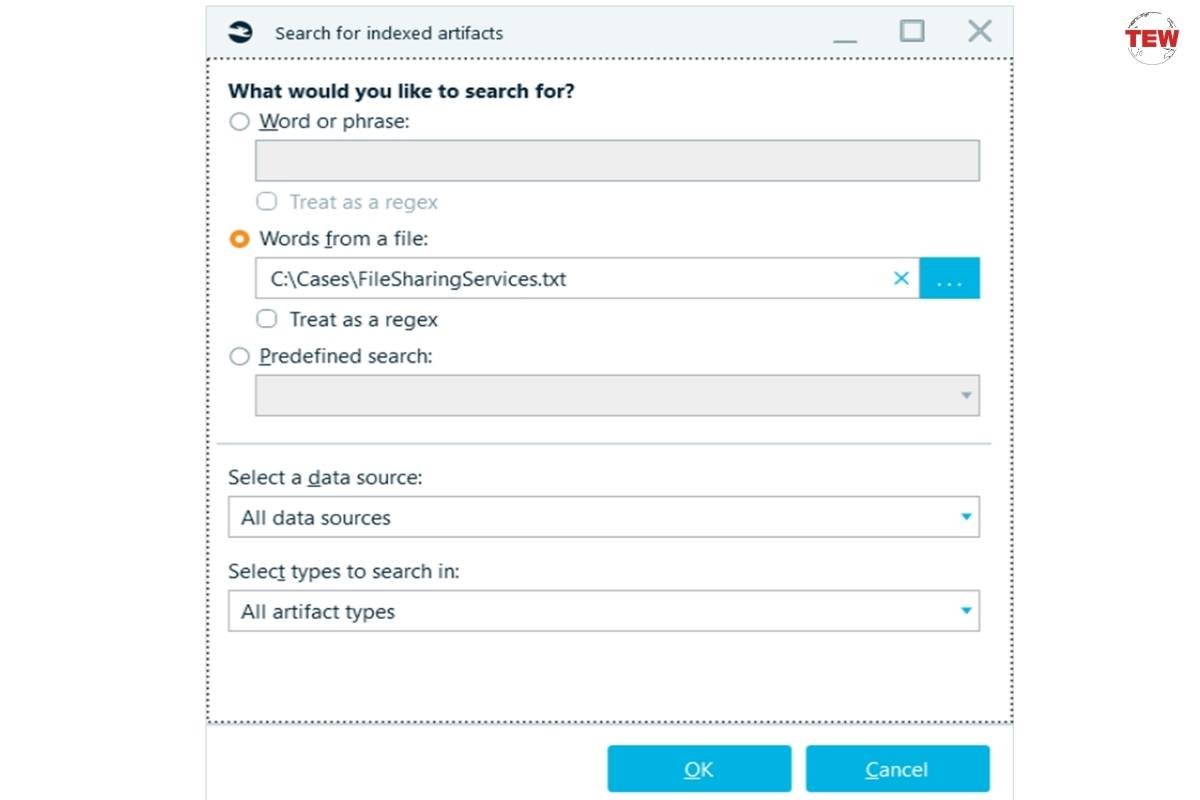
From the search, we inferred that there was a suspicious file with the “Application form.exe” name. We then ran another search to see where it left traces on the computer.
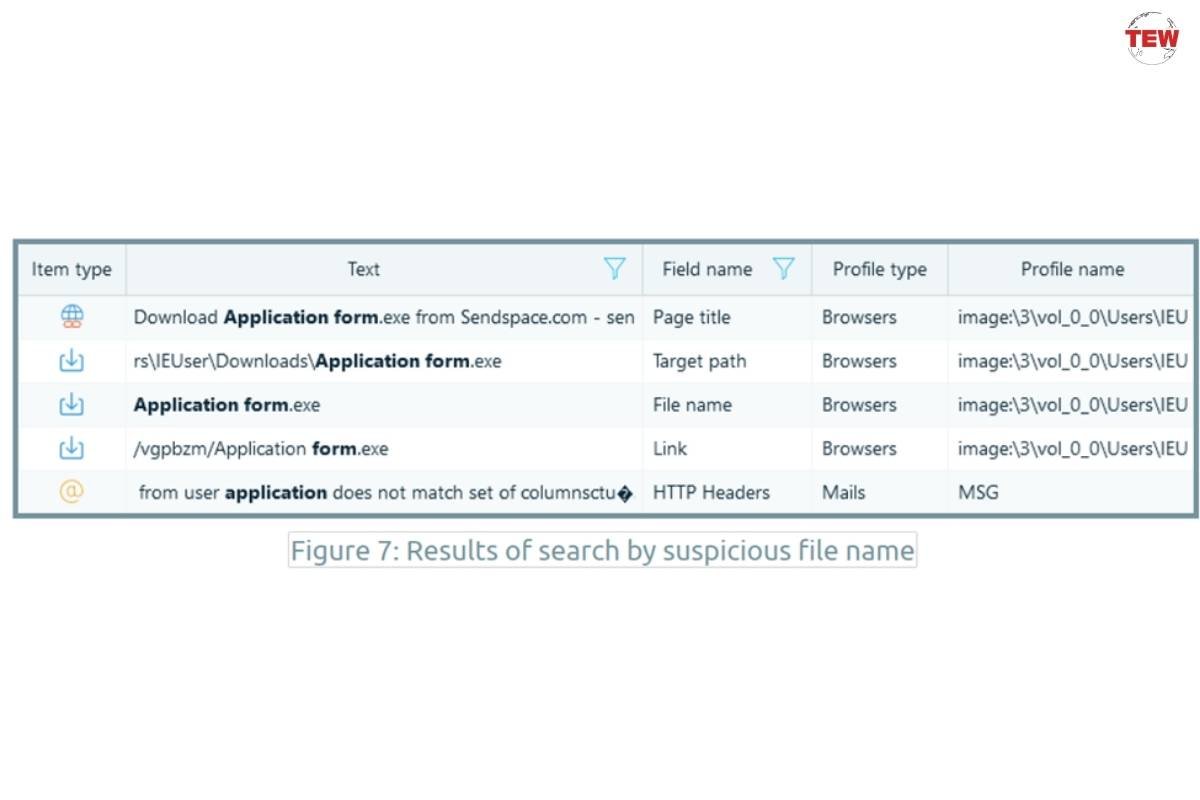
Belkasoft also allows you to see the sources of artifacts. The most important artifacts (based on sources) are those related to web browsing activity.
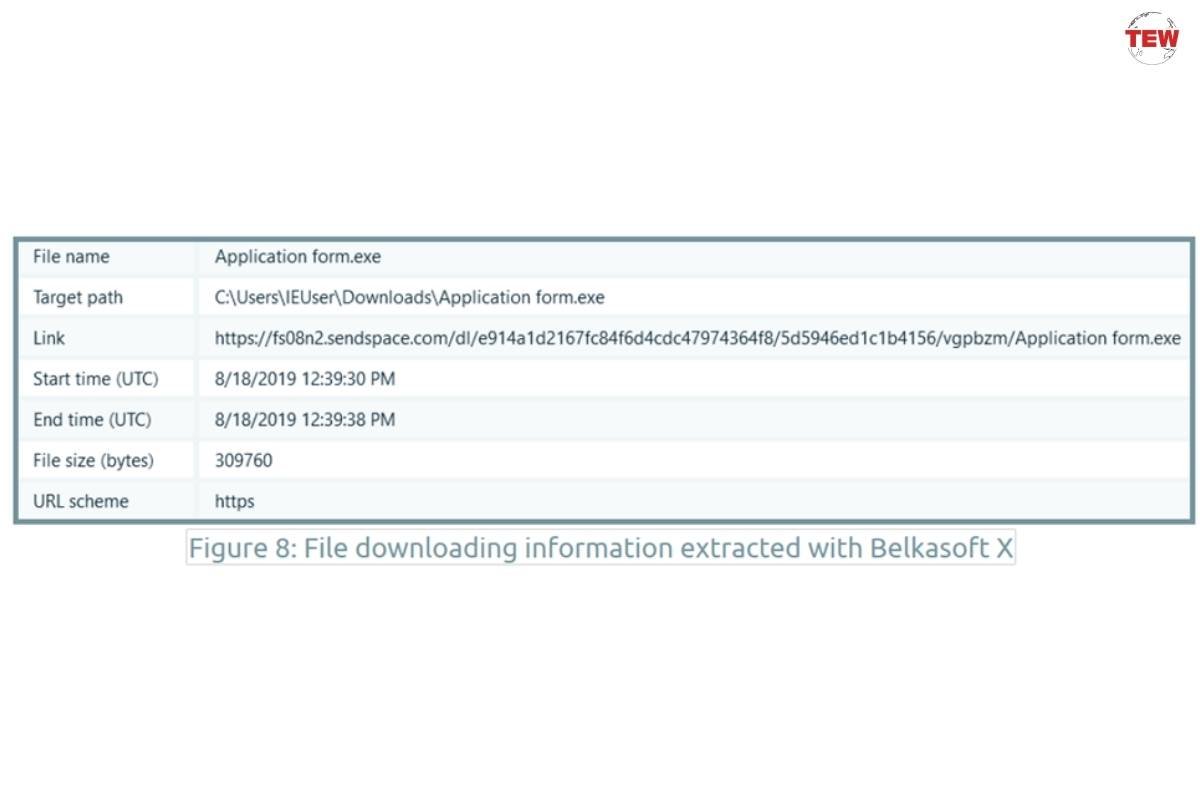
On the screen above, the file was downloaded from SendSpace—a file sharing service, which is quite popular among cybercriminals.
Using Belkasoft Evidence Center X, you can recover traces of deleted web browser histories, especially in a scenario where a user deleted their web browsing history (for any reason). To perform such a task, opt to “carve” data out of your data source:
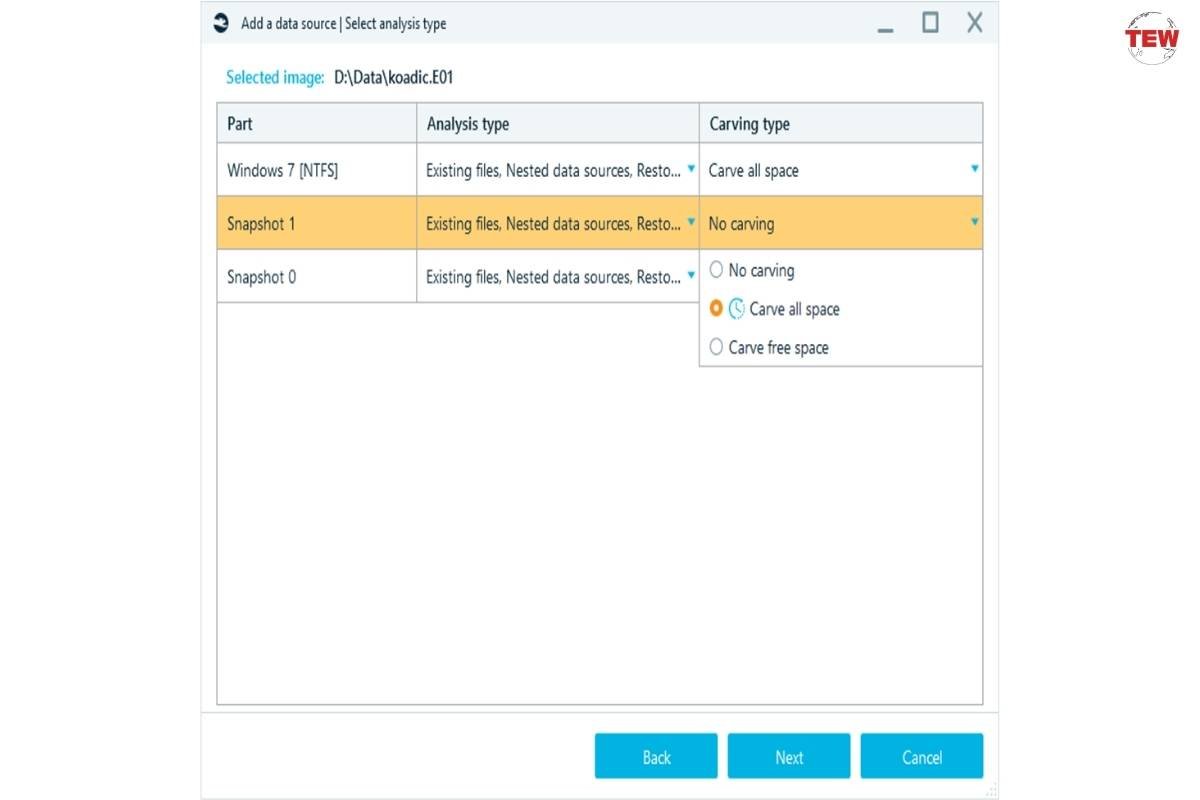
The results from the carving operation will be presented under their respective nodes. In the screenshot below, for example, you can see the carved URLs related to the Tor browser:

5. USB device usage history analysis
Weaponized Office documents and malicious/compromised websites are not the only sources of malware. Malicious files are also easily distributed through USB drives. For example, an advanced banking malware — known as Dark Tequila, which targeted users in Mexico—was distributed not only through phishing emails but also infected USB drives.
Hardware additions—carried out through USB Rubber Ducky, for example— constitute another initial access technique. They allow hackers and penetration testers to perform keystroke injection attacks.
Belkasoft Evidence Center can identify USB devices used by attackers for payload delivery or find traces of malicious devices that were plugged into a computer.
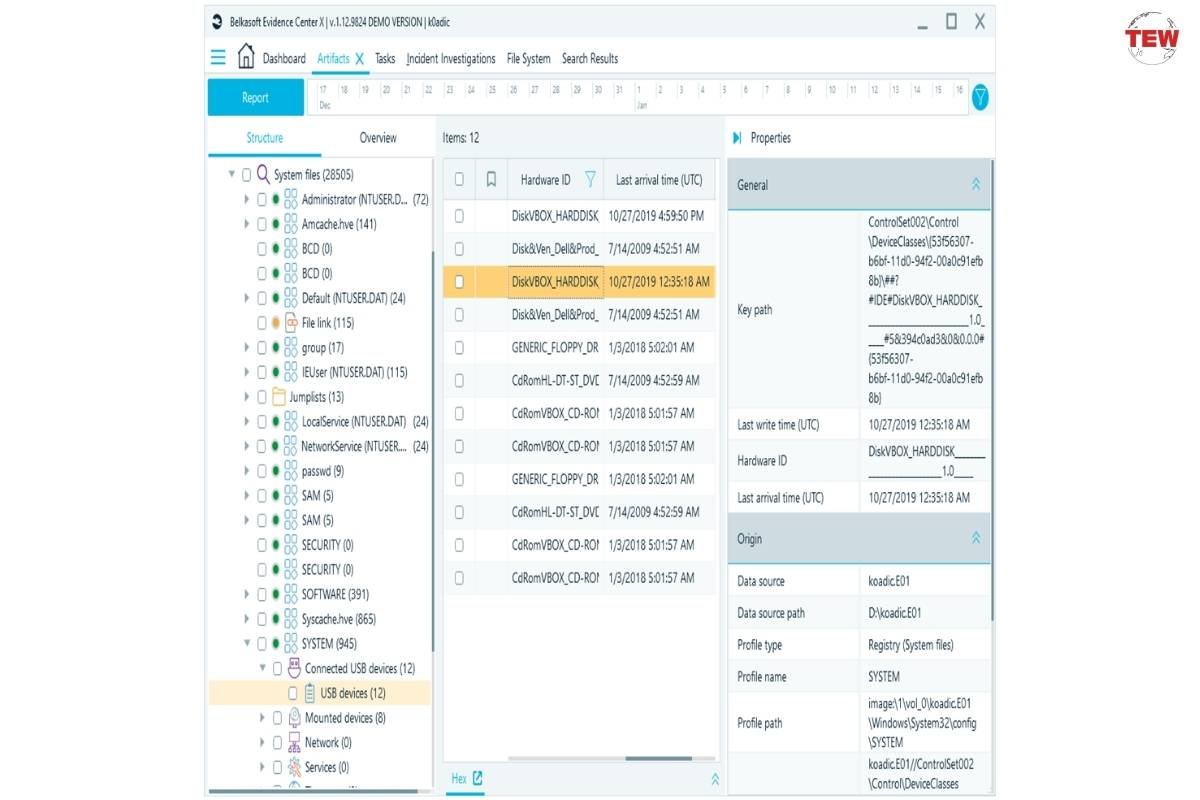
You should not stop at finding out what USB devices were attached. Ideally, you must go a step further to learn what drive letters were used for the mounting. This way, you get to reduce the number of artifacts that have to be examined later.

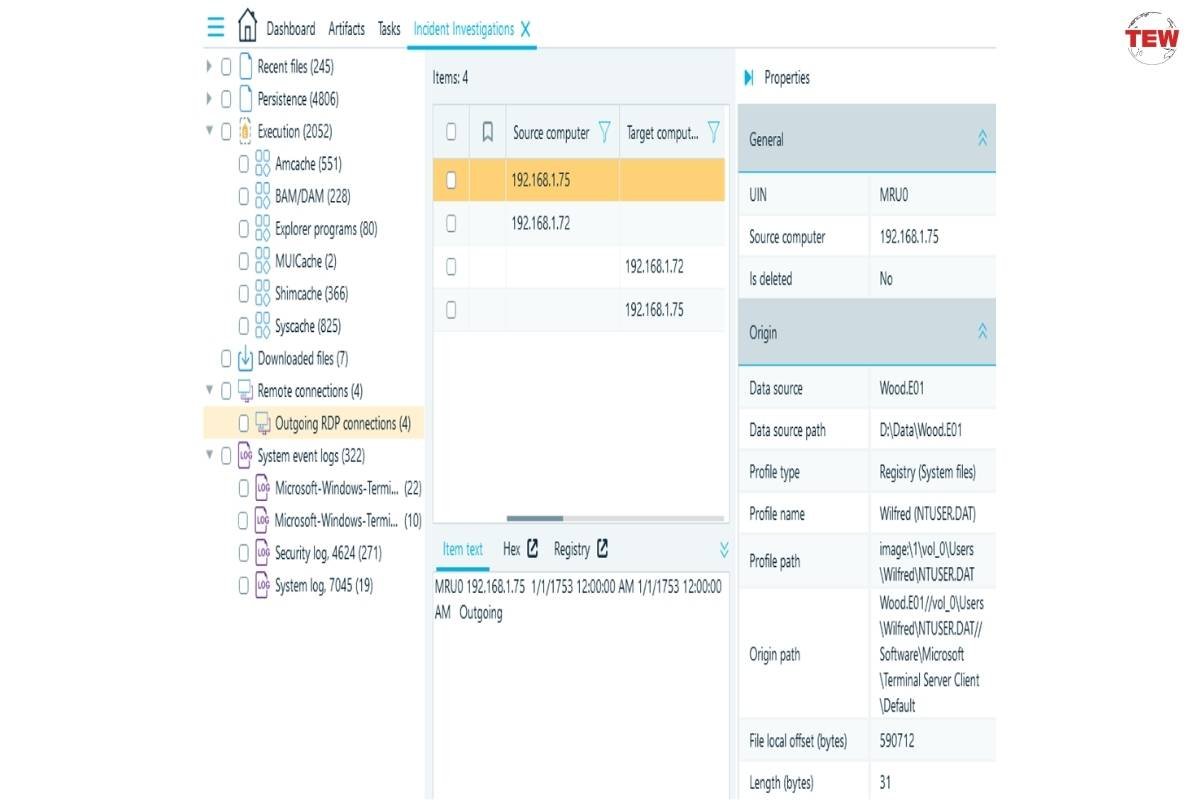
6. RDP connection analysis
And finally, we have RDP servers exposed to the public. RDP brute force attacks are commonly used in distributing ransomware and crypto miners. An attack might be initiated from a single login—since there are many dark web shops selling credentials for compromised servers.
With Belkasoft X, you can easily filter Windows event logs to find evidence of RDP connections. To do this, navigate to the Incident Investigation window and select the Remote connections node:
Conclusion
In this article, we reviewed the simple ways through which attacks to an endpoint start. We also described a basic incident investigation plan to identify the initial infection vector.
Where necessary, we illustrated the process using Belkasoft X.
Belkasoft Evidence Center X is a digital forensics and incident response tool that is commonly used for incident response and investigations—since it significantly reduces the time needed for finding and analyzing the initial access vector used by an attacker. Belkasoft solutions for corporate customers are designed to help you deal with various data breaches and respond in a quick manner to prevent data losses in the future.






